Infrastructure as a Service (IaaS) – Azure Hybrid Infrastructure
Introduction
As one of my first steps into the world of ‘Azure’, I wanted to take a look at the idea of transition. This tutorial is taking the approach from an ‘Azure’ starter and scoped to the technical implementation.
During the same time, I am looking to also write the business ‘why’ case; why would I as a business do this and what are the benefits and flaws… lets be straight; I work with technology and am not a salesman, there are two sides to the coin, no matter whom tries to hide the fact.
Scenario
I want to keep my onsite services, but extend into Azure as a seamless hybrid approach, looking at how the various service opportunities can communicate and the how to ‘best plan for the future’ from a varying point of view. So, first topic to cover is connecting the world of Azure to my onsite infrastructure with the use of a Site-to-Site VPN.
- As an overview, the following components are required:
- Azure: Microsoft’s could offering
- A subscription in Azure: allowing yourself to use the service
- A virtual Network: created in Azure, think of it like your physical network infrastructure in the cloud
- Subnet: Network segments
- On-site Premise: your onsite infrastructure
- On-site VPN device: a device that will be the termination point at the edge of your onsite and also the access point into your infrastructure.
Now, the saying ‘a picture can paint a thousand words’ is my approach in most of my personal learning; I also think this seems to work with most people and therefore let’s start with a picture:

Not quite the correct hair colour (also a little too much). But this is my mindset in approaching Azure, with the amount of terminology and abbreviations; saying that, I think this is the same with any new technology, so rather than focus on a list of terms at the start, I will summarise at the end of the tutorial, rather than the start.
Key Data Technical Required
Do not worry if you do not understand each element or term, as you proceed through the tutorial.
Example data has been used in the table and will be used throughout the tutorial, however the hope is by the end, that you will understand exactly what the particular data is used for.
| Virtual Network | ||
| Item | Setting | Description |
| Virtual Network Name | VNet01 | This is our segment of the pie in the virtual azure world; a piece we are cutting out for ourselves |
| Address Space | 10.10.0.0/16 | |
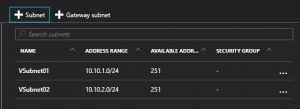
| Subnets | ||
| VSubnet01 | 10.10.1.0/24 | |
| VSubnet01 | 10.10.2.0/24 | |
| Resource Group | VNetwork | |
| Location | West Europe | |
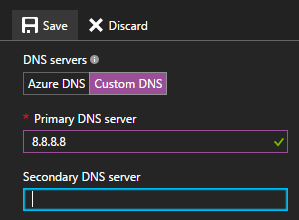
| Custom DNS | ||
| DNS Server | 8.8.8.8 | |
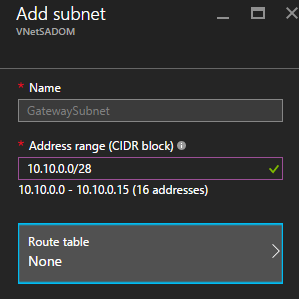
| Gateway Subnet | ||
| GatewaySubnet | 10.10.0.0/28 | |
| Virtual Network Gateway | ||
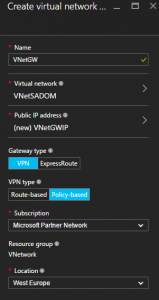
| Gateway Name | VNetGW | |
| Public IP | VNetGWIP | |
| Gateway Type | VPN | |
| Connection Type | ||
| VPN Type | Policy-based | |
| Location | West Europe | |
| Local Network gateway | ||
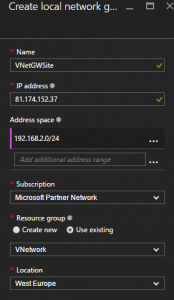
| Local Network Gateway Name | VNetGWSite | |
| On Site VPN Public IP | 81.174.152.37 | |
| Address Space | 192.168.2.0/24 | |
| Location | West Europe | |
| VNetGW01 Connection | ||
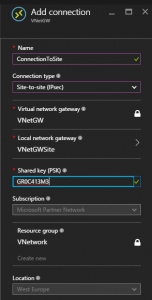
| Connection Name | cnnSite | |
| Connection Type | Site-to-site (IPsec) | |
| Virtual Network Gateway | VNetGW | |
| Gateway Type | VPN | |
| Local Network Gateway | VNetGWSite | |
| Shared Key | GR0C413M3 | |
| Resource Group | Vnetwork | |
| Location | West Europe | |
| SOPHOS UTM: IPSec Remote Gateway | ||
| Name | MSAzureVPN | |
| On Site VPN Public IP | 52.174.148.52 | |
| Shared Key | GR0C413M3 | |
| Remote Network Name | MSAzureNetwork | |
| Remote Network Name | 10.10.0.0./16 | |
| SOPHOS UTM: IPSec Policy | ||
| Name | MSAzurePolicy | |
| IKE Encryption algorythm | AES 256 | |
| IKE Authentication algorythm | SHA1 | |
| IKE SA lifetime | 28800 | |
| IKE DH group | Group 2: MODP 1024 | |
| IPsec encryption algorythm | AES 256 | |
| IPsec Authentication algorythm | SHA1 | |
| IPSec SA lifetime | 3600 | |
| IPsec PFS group | None | |
| Strict policy | unchecked | |
| Compression | unchecked | |
| SOPHOS UTM: IPSec Connection | ||
| Name | MSAzureConnection | |
| Remote Gateway | MSAzureVPN | |
| Local Interface | External (WAN) | |
| Policy | MSAzurePolicy | |
| Local Networks | Internal (my local) | |
| Automatic firewall rules | Checked | |
| Strict routing | unchecked | |
| Bind tunnel to local interface | unchecked |
Setup
My setup is a little different than most, but in the simplest form:
[Example Visio Placeholder]
Process
Create the Virtual network, think of it like your physical network infrastructure, initially without the logical part…. A bit like you have just made yourself a little box inside the cloud…. Has to be somewhere. Whilst create e.g. VNetwork01:
So now I have my Virtual Network Gateway, the edge of my box….
….so now I have to effectively create the virtual customer premise side…your remote part but in Azure
this could be thought of as the edge device on your site network.